CVE-2018-0886: Microsoft Security Update CredSSP affecting RDP Access
On the 8th of May, Microsoft finalized an update which started in March 13th by changing the authentification protrocol of the remote desktop sessions.
They rolled the final update by disabling the former CREDSSP protocol since an exploit was discovered. (CVE-2018-0886)
The exploit allowed to execute remote code a remote system through the logins details provided in a regular remote desktop session.
A hacker could therefore gain access to the remote desktop data, programs or even create/ disable new accounts.
Since, yesterday the patch not only patched the security issue by completely changed the authentification protocol and disabled the CREDSSP one by default.
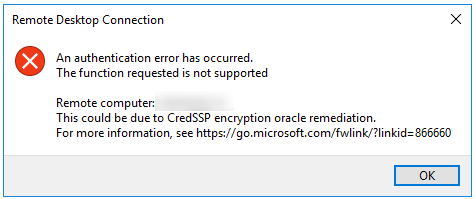
The issue is that if you haven’t updated your Windows VPS (remote desktop server), you wouldn’t be able to access your VPS any longer and you should see the following message:
An Authentification error has occurred.
The Function requested is not supported
Remote computer: *IP ADDRESS*
This could be due to CredSSP encryption oracle remediation.
For more information, see https://go.microsoft.com/fwlink/?linkid=866660
In order to retrieve the usual access to your Windows VPS / Remote Desktop Access you would need to follow the steps below:
- Open a Command Prompt using Administrator Rights (right click on the cmd.exe, select execute as administrator)
- Paste the following commands into your command prompt and hit enter
reg add “HKLM\Software\Microsoft\Windows\CurrentVersion\Policies\System\CredSSP\Parameters” /f /v AllowEncryptionOracle /t REG_DWORD /d 2
It will revert the modification made automatically with the latest automatic Windows Update and you should be able to access your remote desktop again.
Giving how critical this vulnerability is, we warmly invite you to perform all the Windows updates in order to patch the current security issue which is considered as highly critical and put your Windows VPS at risk.
Once you have run the update and your Windows VPS has been restarted, your VPS is patched and if you allow a remote desktop access to your computer, you would need to revert the change made by typing in the command prompt with elevated privileges the following:
reg add “HKLM\Software\Microsoft\Windows\CurrentVersion\Policies\System\CredSSP\Parameters” /f /v AllowEncryptionOracle /t REG_DWORD /d 1
Hit enter.