World Wide Ransomware Outbreak using the NSA ToolKit
Yesterday a massive world wide event took place with a ransomware worm attacking hundreds of thousands of computers and self replicating.
How did the Ransomware spread ?
The ransomware WannaCry (aka : WCry, WanaCryptor, WannaCrypt, Wanna Decryptor)has been seeded first through a campaign of emails phishing and spread to governments services (NHS, Russian Ministries..) and also many corporations (FedEx, Renault, Dacia, Nissan…) and throughout different countries.
After the initial mailing campaign, the ransomware was self distributing by SMB network scan using shared folders.
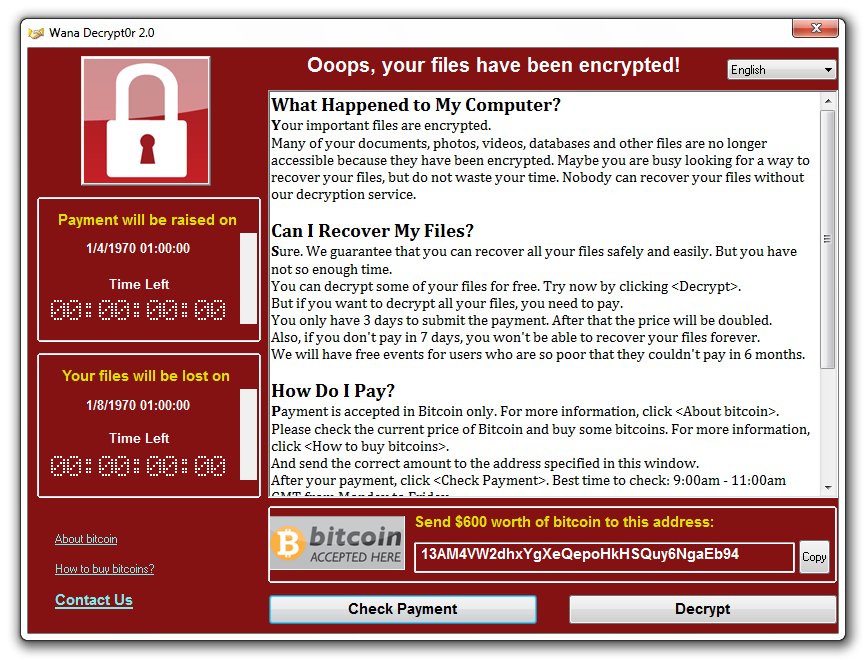
The ransomware was using the NSA Toolkit (Eternal BlueExploit of the toolkit) released for free by a group of hackers called the Shadow Brokers in April allowing anyone to gain access to any Windows based computers within a few minutes. (SMB v1/ RDP protocol).
The malware spreading was contained through a “kill switch” which simply involved a domain registration which was a condition for the malware to keep spreading. If the domain wasn’t resolving then, it would keep attacking. If it resolves then it would stop.
You can find a more detailed and technical approach from a security analyst :
https://www.malwaretech.com/2017/05/how-to-accidentally-stop-a-global-cyber-attacks.html
What Can I do to protect myself and avoid being infected ?
In order to protect yourself, you would simply and urgently need to run all Windows updates for your server.
The backdoors were patched by a Windows updates for all Windows version and even the unsupported (End of Life) Windows XP.
It is recommended to run the windows updates every now and then and in those times more than ever.
It is indeed not quite convenient to have your VPS restarted but it is important to have them set.
You also need to keep a backup of your data not tied to your computer / VPS. (offline hard drive that you plug to back your data up) or an USB key for a lesser amount of data).
For a Windows VPS, if you are using our services, you can simply open a support ticket requesting us to take a backup of your VPS. You can also specify if you would like to be part of the monthly backup or keep a recovery point.
Otherwise, you would need to use a backup system not tied / mounted to your VPS such as a FTP server through a 3rd party client, a cloud based storage with a drag and drop web page for instance.
If you are in a hurry you can also run the commands to patch your servers quicker as introduced by Microsoft :
https://support.microsoft.com
Can a Ransomware affect Dropbox ?
First and foremost, there is an important disclaimer, a common thinking process if you were using a Windows VPS is to use Dropbox as a backup platform. However, if you aren’t a Dropbox Premium users then you are exposed to have your dropbox encrypted. As a premium you would be able to recover your encrypted files by restoring a previous version but not in the free version.
One safe behavior while using dropbox which remains extremely convenient to transfer files from your computer, would be to use the selective synchronization (as explained here ) in order to only synchronize one exchange folder and hide the rest of your files from any Ransomware hitting a VPS.


